Businesses invest millions of dollars in antivirus software each year, but what if the real vulnerability rested with the end user?
One cybersecurity researcher suggests that people’s personalities put them at risk for falling prey to cyber scams.
Colorado Springs-based researcher and cyber-psychologist Dr. Erik J. Huffman said there are 12 key personality traits that make people vulnerable.
Impulsivity, for example, is the No. 1 risk factor that makes some people susceptible to click on suspicious links and attachments without thoroughly vetting them, Huffman said.
Overachievers also are particularly prone to falling for cyberscams because they want to be as efficient and fast as possible and don’t always slow down enough to evaluate emails with links to phishing scams and other tricks intended to steal personal information, Huffman said.
Other traits include one’s social media habits, tech upbringing, self-motivation, agreeableness and whether a person is extroverted or lives alone, among other traits.
In short, it doesn’t pay to be a trusting person on the internet, said Laura Baker, co-founder and executive director for the nonprofit CyberWyoming. In her experience, not only are scammers taking advantage of these vulnerabilities, they’re getting much craftier at doing so.
Expensive Problem
In 2022, Americans lost $8.8 billion to fraud, according to a Federal Trade Commission (FTC) report, which shot up 30% from the prior year.
And Wyomingites are less savvy than other states when it comes to fending off cybercrimes, ranking No. 37, according to a 2023 FTC report.
Among the greatest vulnerabilities are online shopping and negative review scams, with Wyoming topping the list for falling victim to these types of crimes. In total, these scams accounted for just under 19% of all cyber scams in the state, or 617 incidents reported last year, according to the FTC.
Online shopping scams consist of cybercriminals masquerading as legitimate online retailers either on the internet or social media sites, often aping other retailers’ websites and offering luxury items and electronics for a fraction of the price.
Often, they’ll steal other company’s logos and website designs. Sometimes, consumers will receive the merchandise they’ve paid for, though more likely will never see anything.
Baker said one tip off that something’s a scam is the manner of payment with fake stores often requiring payment by money order, preloaded money cards or wire transfers, making it nearly impossible to recoup the lost money.
Negative review scams are the second most common type of scam nationwide, the FTC reports, with more than 75,500 scams reported in the first quarter of 2023.
These crimes involve scammers posting negative reviews for restaurants and businesses on Google Maps or other Google platforms, then exhort the owners by emailing them and offering to remove the reviews for a fee, typically a Google Play gift card in a designated amount.
Don’t Trust Anyone
Baker and her nonprofit keep a running tally of scams reported to them across the state in their weekly Hacker’s Brief.
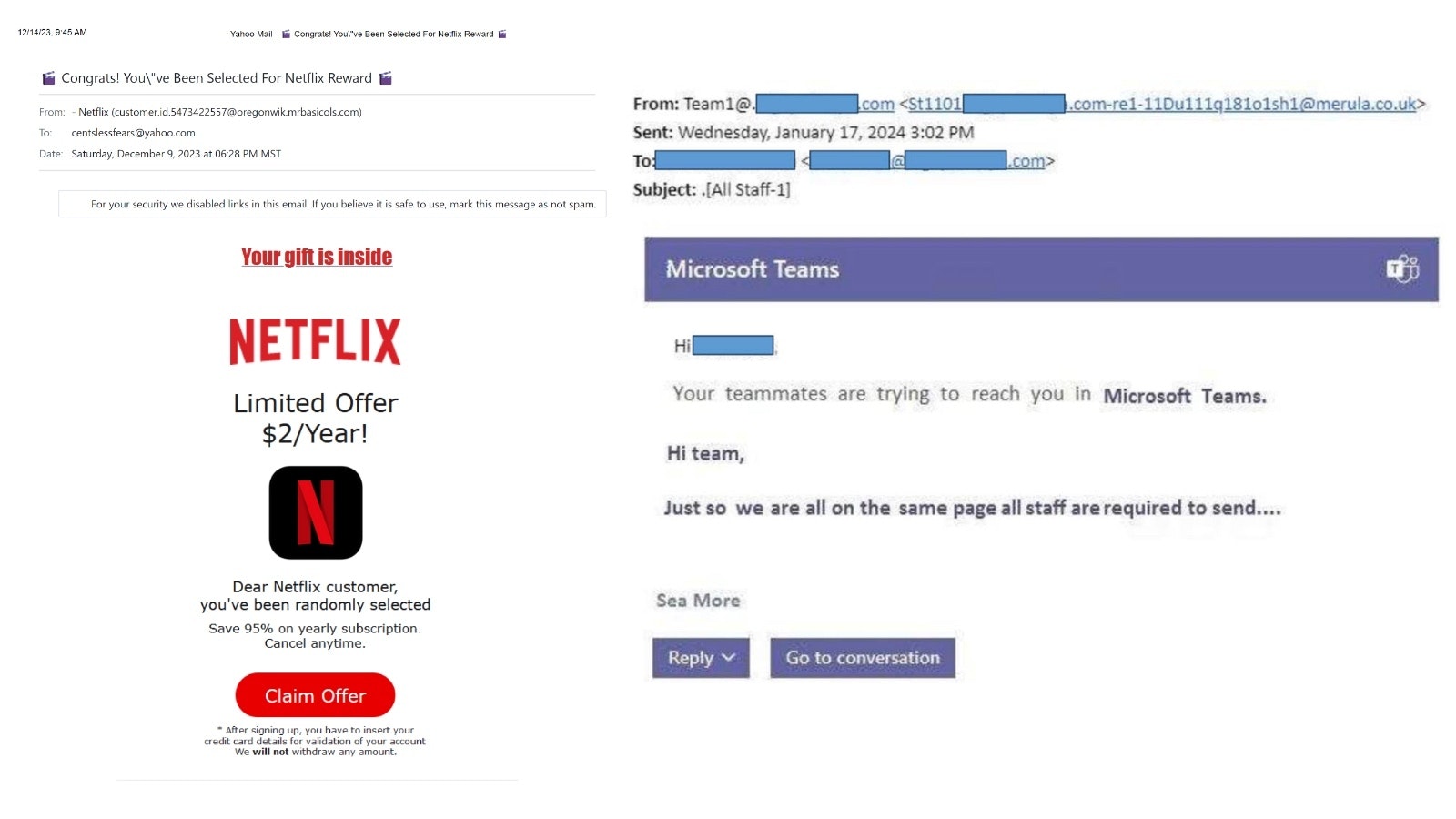
In one recent scheme making its way across Wyoming and beyond, scammers send a fake email, ostensibly from Microsoft Teams, saying that teammates are trying to reach them and asking that person to enter their login info and password.
The screen looks close enough to that of an authentic Microsoft Teams screenshot, though it’s actually an imposter hoping to use the login information to hack into that person’s email.
An impulsive person or one hoping to appear on top of their job might be inclined to enter that information without noticing it’s a scam, Baker said.
One way to mitigate damage should one fall prey to such a scam is to add two-factor authentication to email, bank and other social media accounts and storing the backup authenticator codes in password protected Word documents, Baker said.
Other popular scams making the rounds across the state are the ubiquitous offers from companies like Netflix and Yahoo! offering huge discounts on yearly subscriptions. The user is then asked to claim the offer and provide their credit card information.
One current scam is much more localized involving Blue Federal Credit Union, which Baker said is in the process of updating its software and switching over to a mobile and online app and newer software.
“The hackers have really been trying to take advantage of that,” Baker said. “They’ve been calling and saying that they're from Blue and need your password to test the new system.”
The scams are always changing, and Baker suggests regularly checking Hacker’s Brief, which also allows a person to report scams.
Danger Of Too Much Information
Another trait that tends to make a person vulnerable to cybercrime is oversharing on social media. All of those clues about one’s high school, hometown, college, birthday and names of friends and family members can be used to manipulate a person in any number of scams.
It also creates a permanent digital footprint that can be difficult to control, Huffman said, and can be archived, downloaded or shared without your consent.
“Though it may seem trivial, even the mundane details like your mother’s maiden name, your dog’s name or your birthday make you rife for profiling and easier for criminals to potentially garner passwords to bank and other accounts,” Baker said.
Baker further warned that surveys asking for a pet's name, high school mascot and favorite ice cream are also designed to trick a person out of their password reset questions.
And feel free to not answer security questions accurately, Baker further cautioned. Instead of providing a straight answer for one’s hometown or favorite food, Baker suggested responding with vague generalities such as “a city in Wyoming,” “anything with frosting,” or even random responses to throw a hacker off, like “Liquid Plummer.”
Baker said the key is to protect one’s personal information and avoid oversharing.
Scammers are constantly looking at social media for ways to exploit people, she added.
One current scam involves monitoring social media to discern when a boss or supervisor might be going out of town to a meeting or convention. That “boss” then texts or emails an employee to ask that they purchase Google Play or other gift cards for them, so that they can give them out as gifts at the event.
Essentially, scammers are looking for any information they can use to scam people.
“They are putting half stories behind it to make it sound credible,” Baker said.
One way to mitigate that scam is for bosses to verify in advance of what they would and would not ask employees to do during their absence or to call their supervisor for verification, she said.
Alter-Egos
Regardless of personality types, if Baker had to offer bare-bones advice for staying safe online, she suggests creating an alter-ego online.
Her online personality is “Heather,” who is the polar opposite of herself in that Heather is overly suspicious and trusts no one online.
“Put your power hat on,” Baker said. “Be the person who opens the door with the chain on.”
And most importantly, slow down, she added, and be meticulous before clicking or responding to anything.
“There are ways that you can protect yourself pretty easily,” she said.
Jen Kocher can be reached at jen@cowboystatedaily.com.





